Flow wizard network exchange of visits, the utilization of all software system users to collectively contribute to the principle of sharing; totally different lines of access suppliers attributable to the user's scientific discipline, totally different location, totally different interval, user will simply get a true and effective flow access; same time as a general internet promotion software system, the software system additionally provides a spread of basic functions (sub-page access pop mode, destination uniform resource locator, source URL, curve control) for the user to settle on to use the fundamental functions of the software system, the user will be used flexibly they need access to push demand.
Software options
Easy to use
Simple to use, the user name needn't be registered, and add your own uniform resource locator to begin sharing traffic;
The software system supports flow curve management consistent with their wants, users will management their own traffic size;
The software system supports traffic optimisation options, the users consistent with their own set pop mode, destination uniform resource locator, supply URL;
The software system will be set to begin mechanically, hide receptacle icon, boss key, automatic upgrade function;
Software interface is refreshing, permanent free software system, and current enhancements supported user feedback, the upgrade;
Pure inexperienced software system, the software system is simply one file, while not having to put in full support for Windows 2000, XP, 2003, Vista, Win7 in operation system;
High Security
Software uses self-developed embedded browser supported id est kernel, will effectively block every kind of viruses Trojans download;
Using of malicious URLs sensible identification technology, automatic assortment, filtering malicious URLs;
Deep anti-Trojan, intrusion effectively blocks every kind of viruses Trojans from the web;
To prohibit any pop-up window, and allowed to transfer all types of images, sound, video and other binary files, totally scale back network resource consumption;
Prohibit the published of any web content background music, command the page open and prompt sound actually do "silent" for your service;
True effectiveness
The software is predicated on the the IE kernel independent research and development of embedded browser, access to result real and effective;
The user flexibility to specify the the traffic supply uniform resource locator, to confirm that the flow of the $64000 effective;
Users the flexibleness to specify the destination uniform resource locator, and destination uniform resource locator random access sub-pages, bring traffic to the desired page;
The server showing intelligence management the access frequency of the various periods, totally different times of the day to go to a true and effective frequency;
Software supported the randomness of the network visits, totally bonded access interval, time on page, regional variations, real and effective distribution of freelance scientific discipline segment;
Intelligent analysis software system sub-page links at intervals the positioning, and random access, to confirm that the whole web site are accessed, the user doesn't have to be compelled to register to use it.
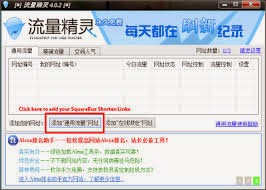
Now you have to choose targeted traffic (any country).
for this click on Number #7.
(1) Worldwided traffic.
(2) Both of this is Chinese only traffic.
(3) Western country traffics only. This will what you'll use mostly.
(4) Custom views or traffics. Allow you to customize the traffic, chinese areas only, so not users here.
Mostly i use 1.
So, if you wanna set the Jingling to western target only, you just have to tick box 3, and save. The four buttons are, from left to right : Save, Default, Reset, Cancel.
Software options
Easy to use
Simple to use, the user name needn't be registered, and add your own uniform resource locator to begin sharing traffic;
The software system supports flow curve management consistent with their wants, users will management their own traffic size;
The software system supports traffic optimisation options, the users consistent with their own set pop mode, destination uniform resource locator, supply URL;
The software system will be set to begin mechanically, hide receptacle icon, boss key, automatic upgrade function;
Software interface is refreshing, permanent free software system, and current enhancements supported user feedback, the upgrade;
Pure inexperienced software system, the software system is simply one file, while not having to put in full support for Windows 2000, XP, 2003, Vista, Win7 in operation system;
High Security
Software uses self-developed embedded browser supported id est kernel, will effectively block every kind of viruses Trojans download;
Using of malicious URLs sensible identification technology, automatic assortment, filtering malicious URLs;
Deep anti-Trojan, intrusion effectively blocks every kind of viruses Trojans from the web;
To prohibit any pop-up window, and allowed to transfer all types of images, sound, video and other binary files, totally scale back network resource consumption;
Prohibit the published of any web content background music, command the page open and prompt sound actually do "silent" for your service;
True effectiveness
The software is predicated on the the IE kernel independent research and development of embedded browser, access to result real and effective;
The user flexibility to specify the the traffic supply uniform resource locator, to confirm that the flow of the $64000 effective;
Users the flexibleness to specify the destination uniform resource locator, and destination uniform resource locator random access sub-pages, bring traffic to the desired page;
The server showing intelligence management the access frequency of the various periods, totally different times of the day to go to a true and effective frequency;
Software supported the randomness of the network visits, totally bonded access interval, time on page, regional variations, real and effective distribution of freelance scientific discipline segment;
Intelligent analysis software system sub-page links at intervals the positioning, and random access, to confirm that the whole web site are accessed, the user doesn't have to be compelled to register to use it.
USE OF JINGLING
(1) Jingling is used to increase your site traffic.
(2) It works on background.
(3) Easy to use.
(4) Generates upto 5000 views a night.
(5) Once configured just one click to start with in future.
(2) It works on background.
(3) Easy to use.
(4) Generates upto 5000 views a night.
(5) Once configured just one click to start with in future.
HOW TO CONFIGURE
- Click the boxed button to add your website url.
CHOOSE TRAFFIC (IMAGE BELOW)
(2) Both of this is Chinese only traffic.
(3) Western country traffics only. This will what you'll use mostly.
(4) Custom views or traffics. Allow you to customize the traffic, chinese areas only, so not users here.
Mostly i use 1.
So, if you wanna set the Jingling to western target only, you just have to tick box 3, and save. The four buttons are, from left to right : Save, Default, Reset, Cancel.
Thats's it .you are done !!!
ADDITIONAL INFO !!!
(1) IPV ratio : Number of subpages an IP will visit. 1:1 means it will only acces the link, and exit. 1:2 means it'll go the the link, find a subpage and clic on it. 1:3 means it will go on main link, find a subpage, clic, find a sub-subpage, and clic.
(2) That will configure the behavior of your links : The first box will behave with the IPV ratio, clicking on random links on the page. The 2nd one will reload the page only. The 3rd one will access a subpage, then open the original link again. The 4th will search for a matching subpage : you can enter what you want in the textbox, the bot will search for it, and access it if it can find it.
(3) Enable or disable popup. Enable it if you site has popups in it. If you're not sure, I'll talk about the Jingling link testing tool later on. If you have popups, you want to set it a 20%.
(4) That's the destination configuration. Used to redirect traffic after a page load. You can add up to 5 links here, and configure a % for each link.
(5) That's the referer. You can change the referer URL here. Add up to 20 links, and chose it's %. For instance, if you set 50% on twitter.com and 50% on facebook.com, you're going to have half of your traffic coming from each of these sites.
(2) That will configure the behavior of your links : The first box will behave with the IPV ratio, clicking on random links on the page. The 2nd one will reload the page only. The 3rd one will access a subpage, then open the original link again. The 4th will search for a matching subpage : you can enter what you want in the textbox, the bot will search for it, and access it if it can find it.
(3) Enable or disable popup. Enable it if you site has popups in it. If you're not sure, I'll talk about the Jingling link testing tool later on. If you have popups, you want to set it a 20%.
(4) That's the destination configuration. Used to redirect traffic after a page load. You can add up to 5 links here, and configure a % for each link.
(5) That's the referer. You can change the referer URL here. Add up to 20 links, and chose it's %. For instance, if you set 50% on twitter.com and 50% on facebook.com, you're going to have half of your traffic coming from each of these sites.
Download Url Below:
Download Here











Did you realize there is a 12 word sentence you can communicate to your partner... that will induce deep emotions of love and impulsive appeal to you buried within his heart?
ReplyDeleteThat's because hidden in these 12 words is a "secret signal" that triggers a man's instinct to love, cherish and look after you with all his heart...
===> 12 Words That Fuel A Man's Love Impulse
This instinct is so hardwired into a man's mind that it will drive him to try better than before to love and admire you.
As a matter of fact, fueling this mighty instinct is so essential to having the best ever relationship with your man that as soon as you send your man one of the "Secret Signals"...
...You will immediately notice him open his heart and soul to you in a way he haven't experienced before and he'll see you as the only woman in the world who has ever truly tempted him.